Consolidated Financial Statements: Process and Tools
Read nowAccounts Payable and Vendor Management
Control your costs with SoftLedger's accounts payable automation and approval workflows.
Accounts Receivable and Customer Invoicing
Collect quicker with recurring and usage-based accounts receivable automation.
General Ledger
Incredibly fast to implement and seamlessly adapting to your business - that's how SoftLedger's smart general ledger empowers your business.
Real-Time Financial Reporting
Enable agile and confident business decisions with SoftLedger's real-time software.
Cash Flow Management
Control your working capital with SoftLedger's cash flow management software and tools.
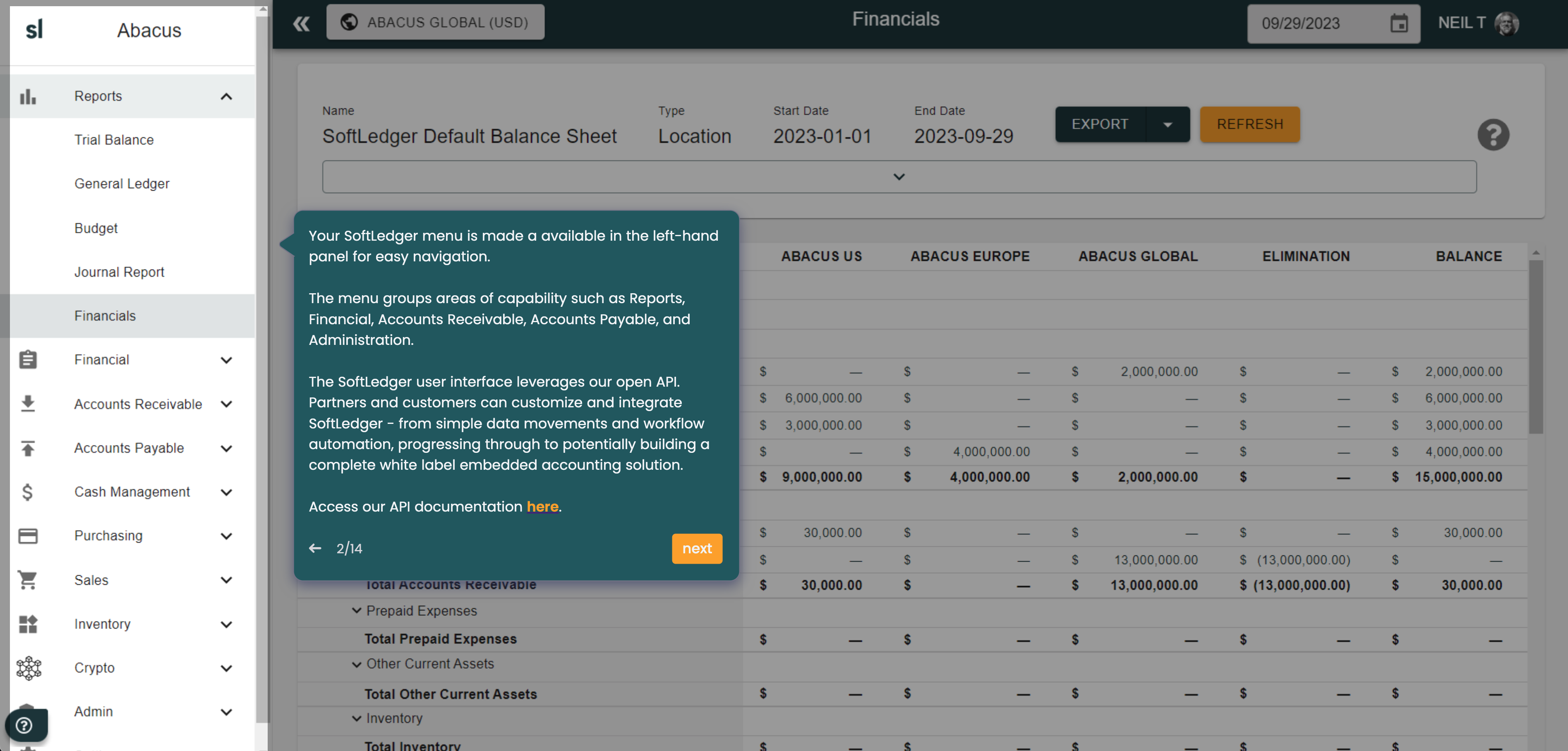
Consolidation Accounting
Instantly centralize your multi-entity, multi-currency accounting with SoftLedger's financial consolidation software.
Multi-Entity Accounting Software
Consolidate multiple businesses, properties and investments, in real-time.
Digital Asset Accounting
Get a powerful crypto accounting software that automates all your cryptocurrency transactions.
Adaptable Subledger
Use only Accounts Receivable, Accounts Payable, or another module as your accounting subledger.
Accounting API
Get a cloud accounting software that is fully programmable via API.
Embedded Accounting
Win more, higher paying deals and increase customer retention with SoftLedger's embedded accounting solution.
Open Banking API Integration
SoftLedger is entirely programmable via the Open Banking API, enabling instant financial data consolidation.
Digital Assets Industry
The ideal tool for tracking your crypto asset management transactions in a scalable way.
Venture Capital
SoftLedger's venture capital accounting software is feature-rich to support all your consolidation needs.
Family Offices
SoftLedger makes it easy to consolidate reporting for family offices in one system.
Private Equity
Get greater visibility into your investment data and harness opportunities as they arise with SoftLedger's sophisticated features.
Financial Services
A full-featured financial services accounting software letting you easily handle multiple entities.
Real Estate Investors & Developers
Overcome complexity by seamlessly consolidating your financials across real estate investments and development projects.
CPA Firms & Accountants
Say goodbye to manually tracking login info and software versions! Find out how SoftLedger helps your accounting office make work easier.
Software Developers
Get our easy-to-use SaaS accounting software and significantly decrease your time spent on operations.
Healthcare
SoftLedger's flexibility enables quick and easy adaptation to the changing healthcare landscape.
SaaS Companies
Our API-capable accounting software makes your subscription management a cinch. Let us show you how.
Retail
Seamlessly track and integrate your inventory with SoftLedger's retail accounting software. Get a demo and see how.
Franchises
If your franchise accounting software isn’t specifically built to manage multiple entities, it could be holding you back from getting the information you need. That's where SoftLedger comes in.
Manufacturing
Easily track your costs and manage your inventory through every stage of production with SoftLedger's manufacturing accounting software.
Nonprofit Accounting
Easily aggregate transactions and activities across your organization with SoftLedger.
Church Accounting
A complete solution built to streamline your faith-based organizations' financial management and accounting processes.